To answer this question I need your OS.
These GUI password dialogs are caused by “polkit”. Try pkexec echo hello.
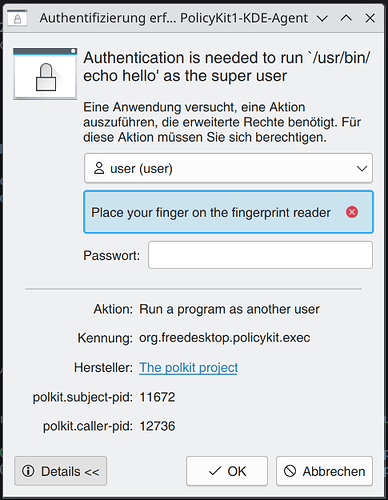
In KDE there is a nice option how to get the polkit action that requires the password.
If you click on “Details” you can see the programs name.
For this exact purpose I created a little script, polkit-helper
Examples of some rules in my /etc/polkit-1/rules.d/
$ cat kdepartitionmgr.rules
polkit.addRule(function(action, subject) {
if (action.id == "org.kde.kpmcore.externalcommand.init" && subject.local && subject.active && subject.isInGroup("wheel")) {
return polkit.Result.YES;
}
});
$ cat org.freedesktop.udisks2.open-device.rules
polkit.addRule(function(action, subject) {
if (action.id == "org.freedesktop.udisks2.open-device" && subject.local && subject.active && subject.isInGroup("wheel")) {
return polkit.Result.YES;
}
});
$ cat 80-udisks2-encrypted-unlock.rules
polkit.addRule(function(action, subject) {
if (action.id == "org.freedesktop.udisks2.encrypted-unlock-system" && subject.local && subject.active && subject.isInGroup("wheel")) {
return polkit.Result.YES;
}
});
$ cat 80-udisks2-encrypted-unlock.rules
polkit.addRule(function(action, subject) {
if (action.id == "org.freedesktop.udisks2.encrypted-unlock-system" && subject.local && subject.active && subject.isInGroup("wheel")) {
return polkit.Result.YES;
}
});
➤ cat 80-libvirt-manage.rules
polkit.addRule(function(action, subject) {
if (action.id == "org.libvirt.unix.manage" && subject.local && subject.active && subject.isInGroup("wheel")) {
return polkit.Result.YES;
}
});
➤ cat firewall.rules
polkit.addRule(function(action, subject) {
if (action.id == "org.fedoraproject.FirewallD1.all" && subject.local && subject.active && subject.isInGroup("wheel")) {
return polkit.Result.YES;
}
});
Your distro may have another action ID for the updates, and I agree they should be automatic and without any password. A weird linux thing, that updates should be manual and require a password. My rpm-ostree rules look like this:
➤ cat org.projectatomic.rpmostree1.rules
polkit.addRule(function(action, subject) {
if ((action.id == "org.projectatomic.rpmostree1.repo-refresh" ||
action.id == "org.projectatomic.rpmostree1.upgrade") &&
subject.active == true &&
subject.local == true) {
return polkit.Result.YES;
}
if ((action.id == "org.projectatomic.rpmostree1.rollback" ||
action.id == "org.projectatomic.rpmostree1.bootconfig" ||
action.id == "org.projectatomic.rpmostree1.reload-daemon" ||
action.id == "org.projectatomic.rpmostree1.cancel" ||
action.id == "org.projectatomic.rpmostree1.cleanup" ||
action.id == "org.projectatomic.rpmostree1.client-management") &&
subject.active == true &&
subject.local == true &&
subject.isInGroup("wheel")) {
return polkit.Result.YES;
}
});
This is a little more complex but shows these things:
- you can group multiple rules in one file
- you can choose if the user needs to be local (not ssh) and active (I dont know what that means, maybe unlocked)
- you can select which group can do what, “wheel” is the sudo user but you could for example create a new group “updates” and everone in that group could get update permissions by a polkit rule
groupadd updates
sudo usermod -aG updates $USER
# adapt the update rule
On most single-user systems its best to allow updates for wheel and call it a day. But in my opinion every user should be able to update, and nothing else.